As you probably know by now, MS is releasing out-of-band Security Updates for Exchange 2013/2016/2019 to combat regularly discovered exploits...it started last year about this time with the HAFNIUM exploit. It only affects on-prem Exchange, according to MS (though I don't know how since Exchange Online is Exchange, but that's beside the point).
I see on lots of forums where Exchange admins mess up their systems by installing the Security Updates wrong; this includes ECP being broken, services not starting, etc. So, I'll show you how to easily install them, error free.
For this, we will be using the command prompt. We WILL NOT use Windows Update and we WILL NOT run the .msp directly.
Hide/Disable The Update
First, you'll want to go to Windows Update and uncheck and hide the Security Update (right-click > hide update).
That means: DO NOT install it from Windows Update, and if you use SCCM/WSUS, stop pushing Exchange Security Updates altogether.
Download the Update
Next, you'll wanna make sure you manually download the correct update, because they are CU-dependent.
For instance, if you are currently up to date on Exchange 2016, which is CU22 as of this writing, you'll want this update:
Install The Update
Once you have it downloaded, save it to your favorite directory on all of your Exchange Servers, like C:\Updates.
**Note** You will need to install the update on Mailbox Servers, CAS Servers (if you've spilt roles in Exchange 2013), Edge Servers, and Hybrid Servers. It's your choice if you want to install it on any Management Tools Servers, but it won't hurt to do so.
Put your server in Maintenance Mode.
**Note** I recommend Maintenance Mode even for single servers, because we don't want anything interfering with the install and since the installer will disable Exchange services, it's better to be safe.
Fire up an Elevated CMD (right-click CMD.exe > Run As Administrator).
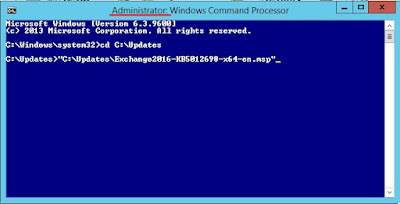
Next, cd to the directory where you saved your install file like so:
cd C:\Updates
Next, in Windows Explorer navigate to the directory and copy the full path by selecting the .msp file and clicking "Copy Path" in the ribbon or SHIFT-Right-Click the file > Copy As Path:
In the CMD window, right-click to paste the path, including the double quotes:
Hit ENTER and the installer will ask if you want to run the file, hit OK and follow the prompts...accept the EULA, next, next a couple times and you're done.
**Note** Some machines will seem to take a loooooooong time during the "calculating space" phase; it could take an hour in some cases. For instance, one of my DAG nodes took 5 minutes, one took 30 minutes, and two took an hour. Let it do it's thing, don't mess with it...rest assured it will go on it's own.
Once the install is finished it may ask you to reboot the machine, go ahead and reboot. If it doesn't prompt you, go ahead and reboot.
Once the server comes back up, take it out of Maintenance Mode and proceed on your next server.
Updated 6/2022:
MS is now releasing SUs (Security Updates) in .EXE format instead of msp, which is supposed to negate running elevated as it automatically extracts to a temp directory and runs using UAC.
They say you can double-click the su.exe file and it will run. Do I advise doing that? NO! It is still safer to run the .exe using the instructions above (in an elevated CMD) to make sure it runs with proper permissions...just copy the path of the exe instead of the msp.
Congrats, you're done! Now you should be patched up to date, with healthy servers...which means all services are running and ECP/OWA works!


No comments:
Post a Comment